What you’ll accomplish
- Create an Okta OAuth 2.0 application
- Assign admin roles to the app
- Provide June with your client ID and tenant URL
- Enable automated identity data ingestion
Capabilities
Once connected, June provides the following capabilities for Okta:Data Synchronization
| Capability | Description |
|---|---|
| Sync all employees | Sync all your employees into June. For IDP integrations, this is always on. |
| Sync Software Applications | Sync all your software applications into June. |
| Sync locations | Sync all your office locations into June. |
Security Actions
| Capability | Description |
|---|---|
| Expire user password in Okta | Expire a user’s password in Okta, forcing them to change it on next login. This is a security action used for compromised accounts or password policy enforcement. |
| Reset user MFA in Okta | Reset all MFA factors for a locked out user in Okta. This removes all enrolled MFA factors and allows the user to enroll new ones. |
Group Management
| Capability | Description |
|---|---|
| Add user to Okta group | Add an employee to an Okta group to grant them group-based access and permissions. |
| Remove user from Okta group | Remove an employee from an Okta group to revoke their group-based access and permissions. |
| List Okta groups | Retrieve a list of all groups in Okta. Optionally filter by search query to find specific groups by name. |
| Get Okta group details | Retrieve detailed information about a specific Okta group including its members. |
Prerequisites
Before starting the integration, ensure you have:- Okta Super Admin access
- Access to create OAuth 2.0 applications in Okta
Okta OAuth 2.0 Application setup
Step 1: Add June Application in Okta
Access Integrations
- Log into June
- Navigate to Integrations page
- Choose “Okta” from the available integrations
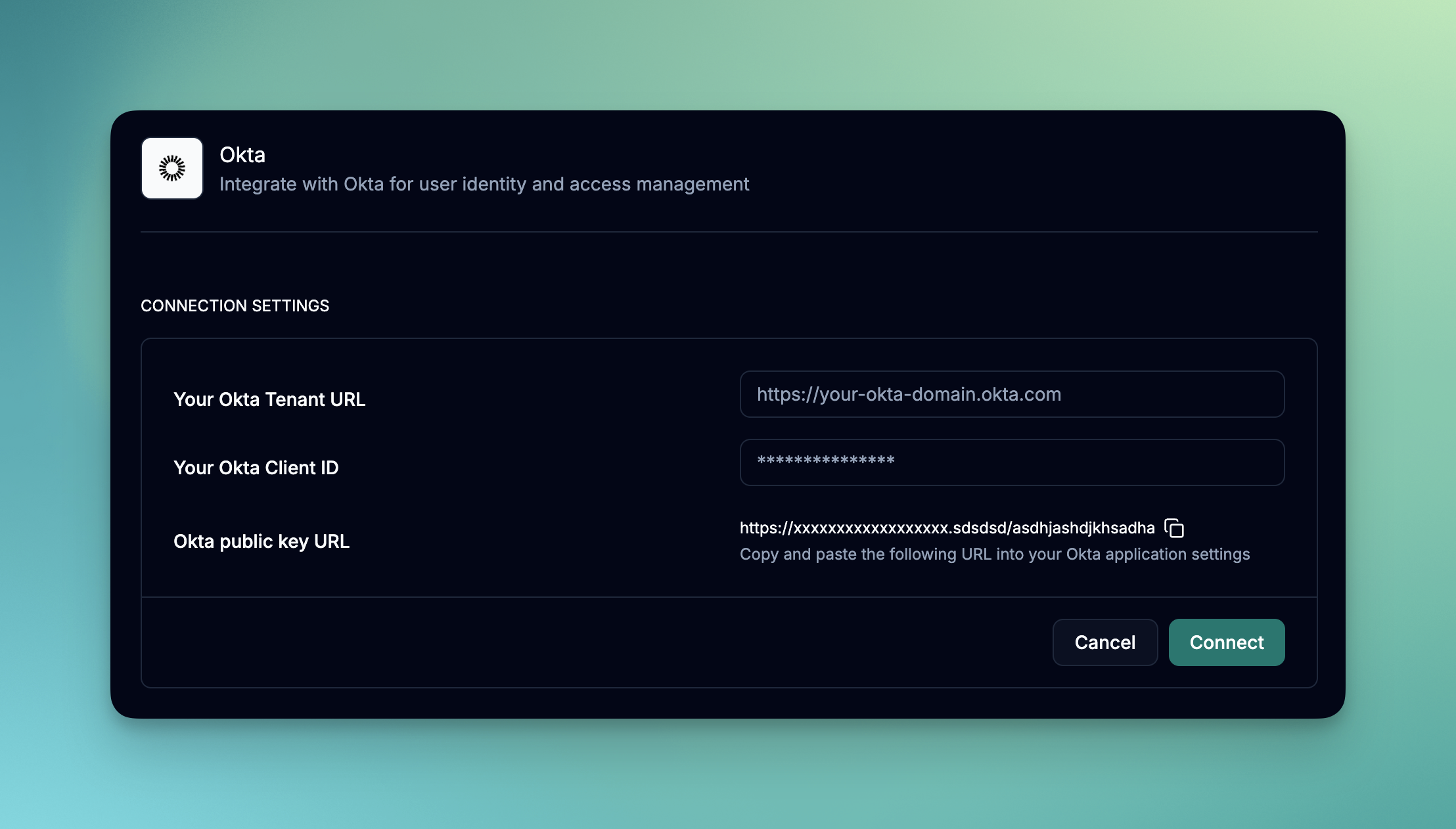
- Before you enter any details, you will need to create an Okta OAuth 2.0 application.
- Copy the Okta public key URL. You will need this for configuring client credentials using PUBLIC KEYS in Okta.
Access Okta Applications
- Log into your Okta admin console
- Navigate to Applications > Applications
- Click Create App Integration
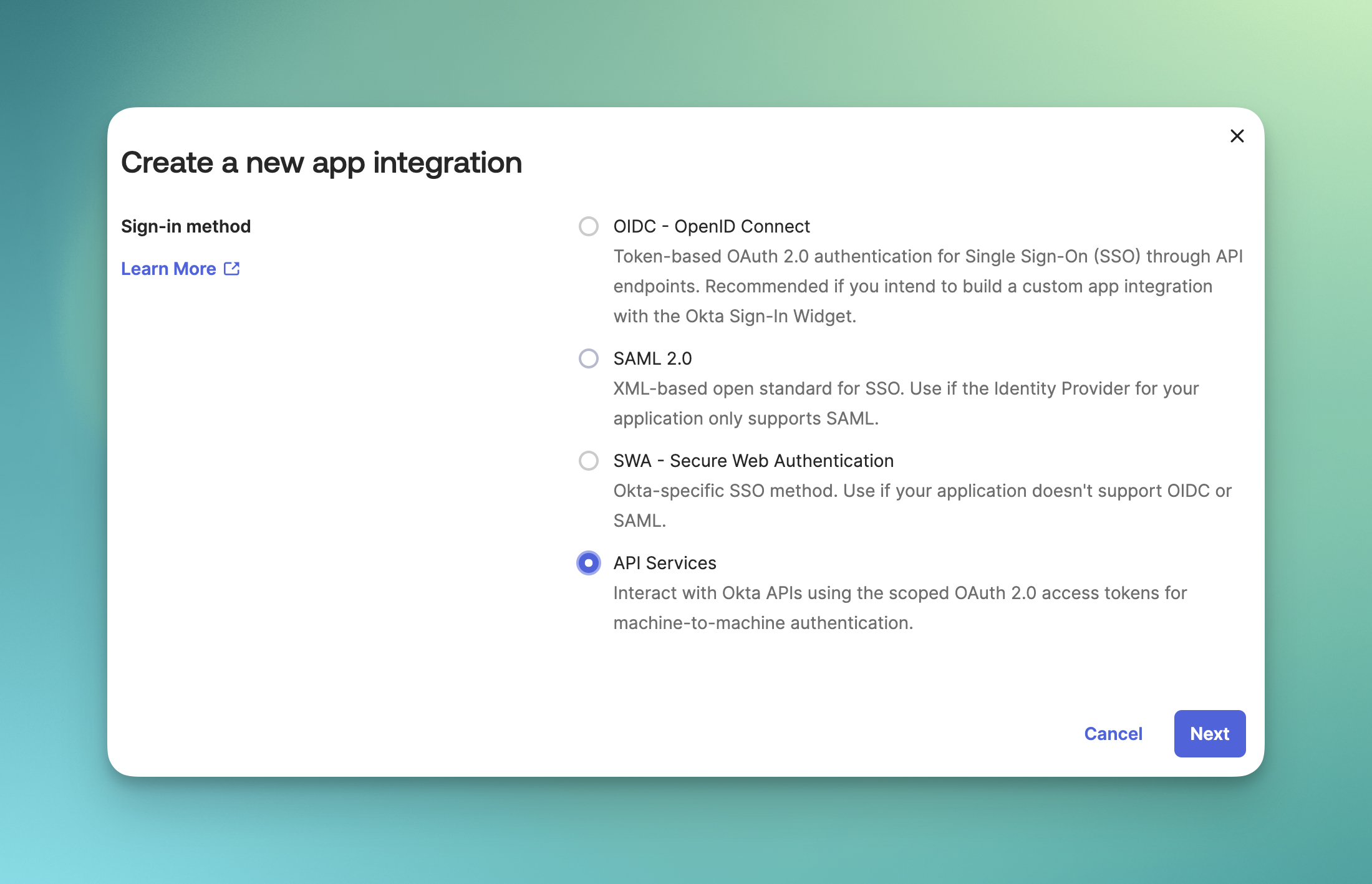
Choose Integration Type
- Select API Services as the sign-in method
- Click Next to continue
- Enter application name: “June API Integration”
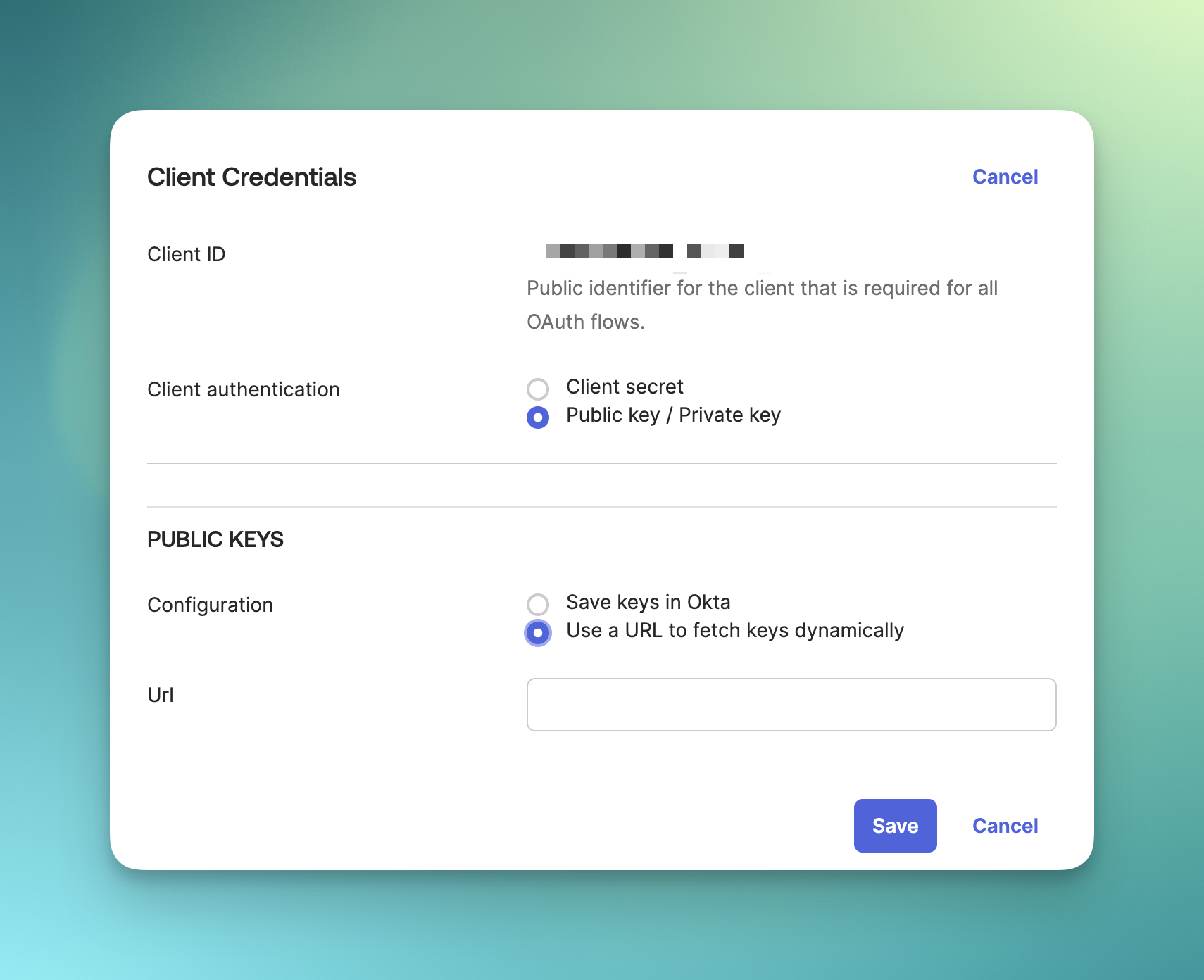
Configure Client Credentials
- Select the June API Integration application
- Go to the General tab
- Click Edit on the Client Credentials section
- Select Public key / Private key option
- Under PUBLIC KEYS, select Use a URL to fetch keys dynamically
- and add the Okta public key URL you copied earlier to the Url field.
- Click Save
Turn off DPoP
- Go to the General tab
- Click Edit on the General Settings section
- Uncheck the Require Demonstrating Proof of Possession (DPoP) header in token requests checkbox
- Click Save
Okta API Scopes
- Go to the Okta API Scopes tab
- Grant the following scopes to the application:
okta.users.readokta.groups.readokta.apps.readokta.logs.readokta.apps.manageokta.groups.manageokta.users.manage
Step 2: Set up Okta Integration in June
Complete Integration Setup
- Go back to June integrations page and select Okta
- Copy the Client ID from the Client Credentials section in Okta and paste it in the Client ID field
- Copy your Okta tenant URL and paste it in the Tenant URL field
- Click Save
- If the integration is successful, you should see a message saying “Integration setup complete” and the Status should be Active.
Test the Integration
- Click on the dropdown menu that has the status of the integration
- Click Test Integration
- If the integration is successful, you should see a message saying “Integration test successful” and the Status should be Active.
- If the integration is not successful, you should see a message saying “Integration test failed” and the Status should be Inactive.
Support Resources
Need help with your Okta integration?- Okta Documentation: Review this article about why June needs admin roles assigned.
- June Support: Contact support for integration-specific assistance
- Community Forum: Join discussions about identity provider integrations
Syncing data from Okta to June may take up to 15 minutes based on the number of users in your Okta environment.